Cyber Incident Response Workflow: A Comprehensive Guide
In today’s digital landscape, the importance of a robust cyber incident response workflow cannot be overstated. With the rise in cyber threats targeting virtual currencies, organizations must ensure they have an effective response strategy in place. Cyber incidents can swiftly disrupt operations, leading to significant financial losses and reputational damage. In this article, we will explore real-world scenarios, provide in-depth solutions, and discuss the associated risks with a focus on enhancing your understanding of incident response.
Pain Points in Cybersecurity
Cyber incidents, such as the infamous 2020 KuCoin hack, where hackers made off with over $200 million worth of cryptocurrencies, showcase the dire need for a thorough incident response plan. Organizations often struggle to address vulnerabilities quickly, leading to extended recovery times and mounting damages. The lack of a well-structured workflow can leave companies paralyzed when faced with an attack. The aftermath of such breaches emphasizes the necessity for a proactive approach to cybersecurity.
Solution Deep Dive
To mitigate cyber risks, a structured cyber incident response workflow is instrumental. Here are the key steps involved:
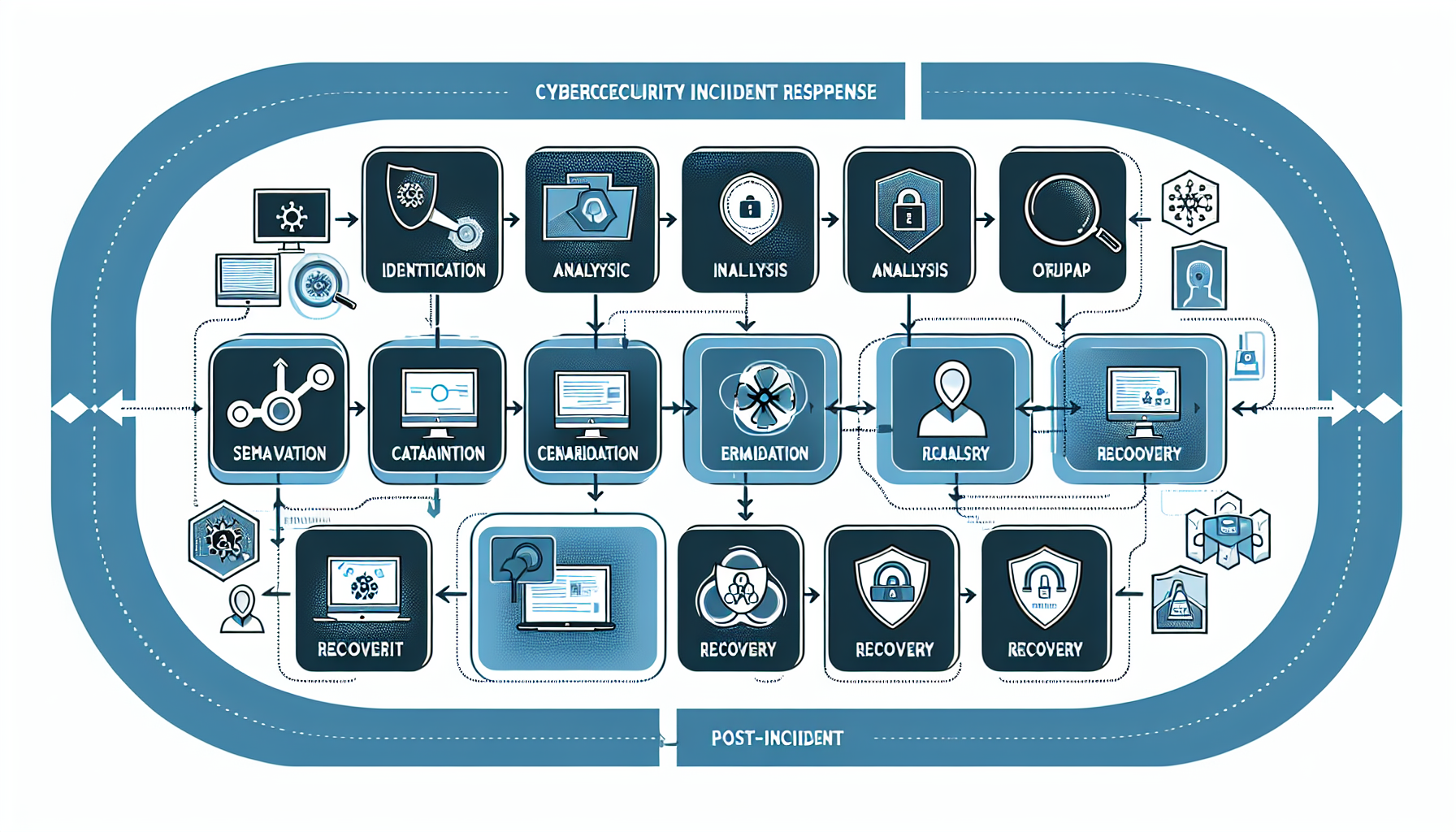
- Preparation: Train your teams and establish communication protocols.
- Detection: Implement advanced threat detection tools to identify anomalies.
- Containment: Isolate affected systems to prevent further damage.
- Eradication: Remove the threats and vulnerabilities that caused the incident.
- Recovery: Restore systems to operational status while ensuring security measures are enhanced.
- Lessons Learned: Conduct a post-incident review to improve future responses.
The effectiveness of a cyber incident response workflow can often be assessed through comparative analysis. Below is a brief comparison of two potential solutions:
| Criteria | Solution A | Solution B |
|---|---|---|
| Security | High | Medium |
| Cost | Expensive | Cost-effective |
| Suitable Scenarios | Large Enterprises | Small Businesses |
According to a 2025 report by Chainalysis, businesses implementing a comprehensive cyber incident response workflow reduced incident recovery time by over 50%, highlighting the importance of a proactive approach in an ever-evolving threat landscape.
Risk Warnings
It’s essential to understand the specific risks associated with inadequate incident response strategies. **Neglecting to establish a clear communication protocol during a cyber incident can lead to confusion and delay in actions taken.** Additionally, lacking regular training can leave your team unprepared for effective response. Consider investing in continuous education and simulation exercises to fortify preparedness.
In conclusion, as cyber threats continue to grow and evolve, a well-defined cyber incident response workflow is invaluable for protecting your organization. At the forefront of cryptocurrency safety, theguter is committed to helping businesses navigate these complex challenges by providing robust solutions tailored to the virtual currency landscape.
FAQs
Q: What is a cyber incident response workflow?
A: A cyber incident response workflow is a structured approach to managing cybersecurity incidents, focusing on preparation, detection, response, and recovery.
Q: Why is it important?
A: It’s crucial as it helps organizations minimize damage, recover quickly, and learn from incidents to strengthen future security measures.
Q: How often should incident response plans be tested?
A: Regular testing, at least quarterly, is recommended to ensure efficiency and effectiveness of the cyber incident response workflow.
Author: Dr. Emily J. Wright, Cybersecurity Specialist with over 15 published papers in cybersecurity research and lead auditor for major blockchain security projects.





