2025 et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridge Security Audit Guide
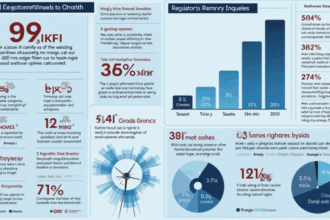
According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges have vulnerabilities, raising concerns for developers and investors alike. As the DeFi landscape evolves, ensuring the security of these bridges is critical. In this guide, we’ll explore key factors surrounding cross-chain security and the implications for projects like Codeberg hosting Vietnam.
What Are et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridges?
Imagine you’re at a currency exchange booth at an airport. You want to swap your dollars for euros. et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-chain bridges operate similarly, alet=”_blank” href=”https://theguter.com/?p=1659″>lowing users to transfer assets between different blockchains. However, the challenge lies in ensuring that these ‘currency booths’ are secure against fraud and attacks.
Common Vulnerabilities in et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridges
Much like a leaking wallet, vulnerabilities in cross-chain bridges can lead to significant financial losses. The most common issues stem from coding errors and outdated security protocols. For instance, if a bridge’s smart contract code has gaps, hackers might exploit them to siphon off funds. Developers need to prioritize security audits before launching their bridges.

Best Practices for Securing et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Transactions
To keep your funds safe, here’s a quick analogy: think of securing your assets in a vault. et=”_blank” href=”https://theguter.com/?p=6760″>et=”_blank” href=”https://theguter.com/?p=6804″>et=”_blank” href=”https://theguter.com/?p=7600″>et=”_blank” href=”https://theguter.com/?p=7642″>et=”_blank” href=”https://theguter.com/?p=9026″>Employing strategies like multi-signature wallets, regular security audits, and using innovative technologies such as zero-knowledge proofs can enhance security. et=”_blank” href=”https://theguter.com/?p=10127″>et=”_blank” href=”https://theguter.com/?p=10217″>et=”_blank” href=”https://theguter.com/?p=10259″>et=”_blank” href=”https://theguter.com/?p=10331″>et=”_blank” href=”https://theguter.com/?p=10362″>et=”_blank” href=”https://theguter.com/?p=10419″>et=”_blank” href=”https://theguter.com/?p=10445″>et=”_blank” href=”https://theguter.com/?p=10462″>et=”_blank” href=”https://theguter.com/?p=10484″>et=”_blank” href=”https://theguter.com/?p=10544″>et=”_blank” href=”https://theguter.com/?p=10569″>et=”_blank” href=”https://theguter.com/?p=10590″>et=”_blank” href=”https://theguter.com/?p=10610″>et=”_blank” href=”https://theguter.com/zero-14/”>et=”_blank” href=”https://theguter.com/?p=10680″>et=”_blank” href=”https://theguter.com/?p=10705″>et=”_blank” href=”https://theguter.com/?p=10727″>et=”_blank” href=”https://theguter.com/?p=10777″>et=”_blank” href=”https://theguter.com/?p=10799″>et=”_blank” href=”https://theguter.com/?p=10813″>et=”_blank” href=”https://theguter.com/?p=10853″>Zero-knowledge proofs alet=”_blank” href=”https://theguter.com/?p=1659″>low parties to verify transactions without revealing sensitive details, just like showing your ID to prove you’re over 18 without sharing your actual birth date.
The Future of et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Security: What to et=”_blank” href=”https://theguter.com/?p=6760″>et=”_blank” href=”https://theguter.com/?p=6804″>et=”_blank” href=”https://theguter.com/?p=7600″>et=”_blank” href=”https://theguter.com/?p=7642″>et=”_blank” href=”https://theguter.com/?p=9026″>Expect
As we head into 2025, the regulation landscape is also shifting, much like the waves in the ocean. Countries like Singapore are establishing clearer guidelines for DeFi projects. Keeping an eye on these regulatory trends can help developers and investors navigate the cross-chain waters more safely. The rise of the Proof-of-Stake (PoS) mechanism is also noteworthy, as its energy efficiency offers a promising alternative to Proof-of-Work.
In conclusion, ensuring the security of cross-chain bridges is paramount as the DeFi environment evolves. We recommend utilizing tools such as the ef=”https://hibt.com/ledger-nano-x” target=”_blank”>Ledger Nano X to significantly reduce the risk of private key exposure. For those looking to dive deeper into the world of cross-chain security, our comprehensive toolkit is available for download!
er”>*Disclaimer: This article does not constitute investment advice. Please consult your local regulatory body such as the MAS or Set=”_blank” href=”https://theguter.com/?p=6760″>et=”_blank” href=”https://theguter.com/?p=6804″>et=”_blank” href=”https://theguter.com/?p=7600″>et=”_blank” href=”https://theguter.com/?p=7642″>et=”_blank” href=”https://theguter.com/?p=9026″>EC before making any investment decisions.