2025 Cross-Chain Bridge Security Audit Guide
According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges have vulnerabilities, which poses significant risks for investors and developers alike. In this article, we will explore the implications of these findings within the realm of Jenkins cloud AWS Vietnam, showcasing the critical importance of security audits in modern financial transactions.
What are Cross-Chain Bridges?
To put it simply, a cross-chain bridge functions like a currency exchange booth at the market, allowing different blockchain networks to communicate with each other. Imagine wanting to trade your dollars for euros at a booth. You hand over your cash, and the booth operator gives you the euros. Cross-chain bridges allow for similar conversions between different cryptocurrencies, enabling interoperability across various blockchains.
Why Do Vulnerabilities Exist?
You might wonder, why on earth would so many bridges have vulnerabilities? Think of it like building roads in a city — as more roads are added, the risk of potholes and other issues increases. Similarly, as more features and capabilities are integrated into cross-chain bridges, the complexity grows, and developers can overlook essential security measures. Jenkins cloud AWS Vietnam stands as a robust platform, but without proper audits, even the most fortified systems are susceptible.
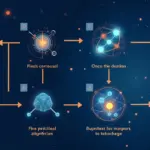
Impact of Zero-Knowledge Proofs
Now, let’s talk about zero-knowledge proofs, which are like a secret code that lets one party prove to another that they know a value without revealing that value. This technology could significantly mitigate risks in cross-chain interactions by keeping user transactions confidential and secure. In a world where data breaches are frequent, implementing zero-knowledge proofs can act as an additional safety net for users engaging with services on Jenkins cloud AWS Vietnam.
How to Ensure Security?
So, how can you protect yourself in this space? First, conduct thorough audit checks on cross-chain platforms before transacting. Think of it like checking the safety of a ride at the amusement park before jumping in. Utilizing tools like Ledger Nano X can reduce the risk of private key leaks by up to 70%, adding an extra layer of security for your digital assets.
In conclusion, as cross-chain technology progresses, so does the need for rigorous security audits. Understanding the insights from Jenkins cloud AWS Vietnam and its implications can empower users to navigate the complexities of DeFi with confidence. For detailed guidance and to download your security toolkit, click here.