2025 Cross-Chain Bridge Security Audit Guide
According to new Chainalysis data, a staggering 73% of global cross-chain bridges have vulnerabilities. As the demand for interoperability grows, it’s crucial to understand how to protect these financial gateways effectively.
What is a Cross-Chain Bridge?
Imagine a cross-chain bridge as a currency exchange booth at the market. Just like you need a secure place to swap your dollars for euros, blockchain networks require secure methods to exchange assets across different chains. As technologies like Content generation AI Vietnam advance, understanding these tools will be vital to your trading strategy.
Common Vulnerabilities in Cross-Chain Bridges
Consider the horror stories of market stalls where money has been lost due to untrustworthy operators. Similarly, many bridges are susceptible to attacks that exploit coding errors or security flaws. To protect yourself, stay informed about potential risks, and be knowledgeable just like you would be when handling cash—keep an eye on who you trust!
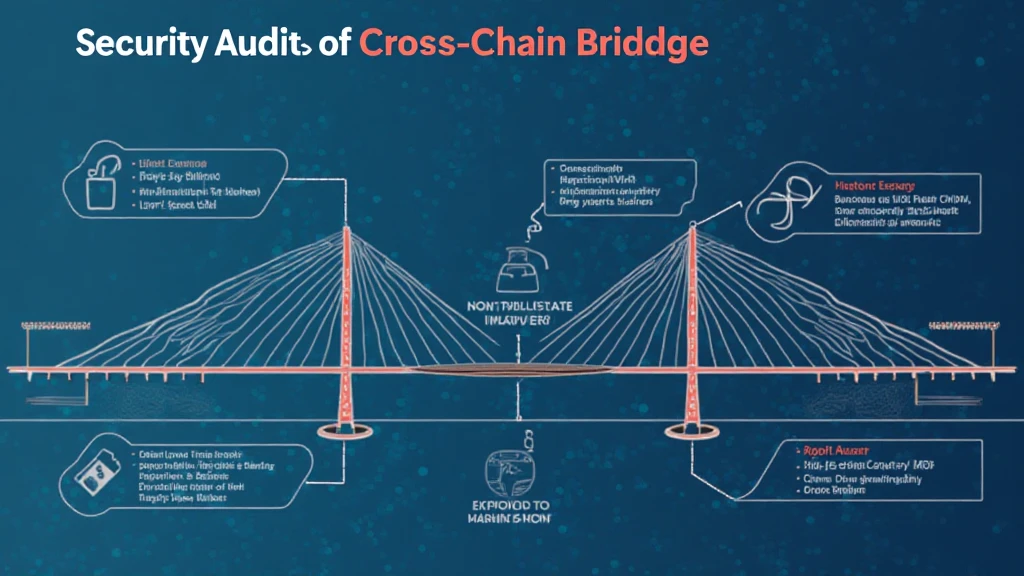
How to Identify a Secure Bridge?
Just like how you verify if a market stall is reputable by checking customer reviews, you can assess a bridge’s security by reviewing its audit reports. Look for reputable third-party audits and transparency in operations. Platforms utilizing robust technologies such as zero-knowledge proofs showcase innovative ways to secure transactions and verify user identity without revealing personal information.
The Future of Cross-Chain Interoperability
In 2025, as adoption of cross-chain solutions increases, we could see new regulatory frameworks emerge, especially in regions like Dubai where crypto regulations are rapidly evolving. Being aware of local laws, such as the Dubai cryptocurrency tax guidelines, is just as crucial as understanding technical aspects to minimize risks when engaging in decentralized finance (DeFi).
In conclusion, as the landscape of cross-chain bridges develops, leveraging tools—for example, Ledger Nano X to reduce private key leakage risks by 70%—is essential. Educating oneself about these technologies is crucial in this ever-evolving environment.
For more insights, don’t forget to download our comprehensive toolkit on cross-chain security. Stay informed and protect your investments wisely!