Understanding HIBT Security Incident Response Timeline
With $4.1B lost to DeFi hacks in 2024, understanding the HIBT security incident response timeline is crucial for cryptocurrency platforms. The rapid surge in blockchain adoption, particularly in Vietnam where user growth rate has reached 180%, emphasizes the need for robust security protocols. In this article, we will outline effective strategies to mitigate risks associated with potential security incidents.
The Importance of a Security Incident Response Timeline
Every time a security issue arises, having a structured response timeline is essential. Think of it like a fire drill in a bank—when a crisis strikes, everyone knows their role. The HIBT security incident response timeline lays out the steps to identify, contain, and resolve security threats effectively.
1. Initial Detection
- Monitor Transactions: Utilize blockchain analytics tools to detect anomalies.
- Incident Reporting: Encourage users to report suspicious activities.
In 2025, tools like Chainalysis will play a pivotal role in this phase, as noted by the firm’s latest report on cybersecurity threats.
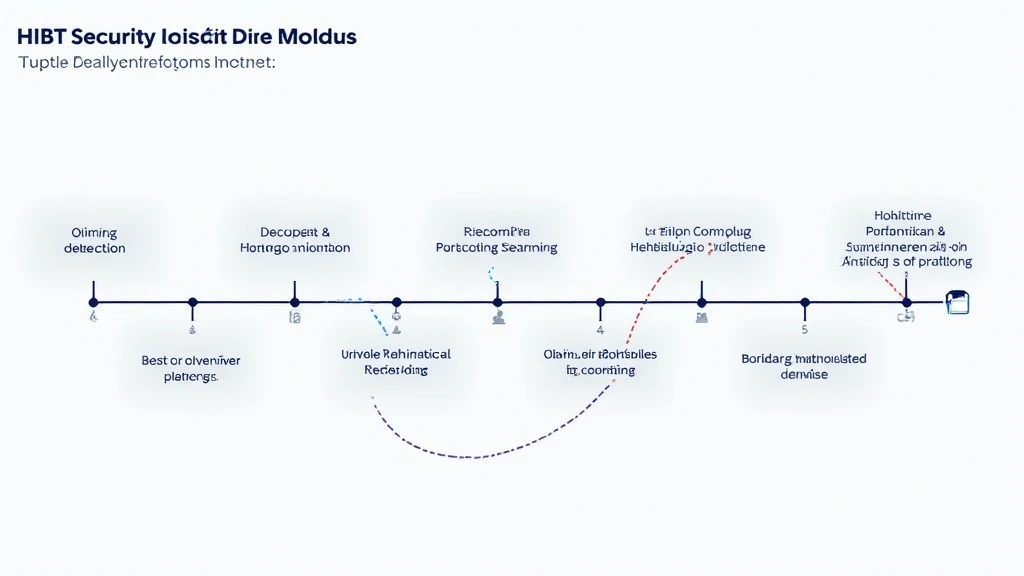
2. Containment and Assessment
- Isolate Affected Systems: Ensure compromised assets are secured to prevent further damage.
- Perform a Damage Assessment: Evaluate the extent of the breach to inform further actions.
This stage is akin to closing the vault and assessing damage after a bank heist.
3. Communication
- Notify Stakeholders: Update investors and clients transparently about the incident.
- Coordinate with Law Enforcement: In severe incidents, collaboration with authorities is essential.
According to HIBT’s guidelines, maintaining clear communication can safeguard a platform’s reputation.
4. Recovery and Learning
- Restore Systems: Gradually return to normal operations while ensuring systems are fortified.
- Conduct a Post-Incident Review: Identify lessons learned to improve future incident response strategies.
As seen in the recent Vietnamese crypto market expansion, companies must adapt their security measures constantly.
5. Continuous Improvement
- Regular Security Audits: Implement routine assessments of protocols and systems.
- Stay Informed: Keep abreast of the latest security trends and threats.
As the blockchain world evolves, aligning with tiêu chuẩn an ninh blockchain becomes indispensable for platforms.
To summarize, an effective HIBT security incident response timeline is integral to navigating the challenges of modern cryptocurrency platforms. By following these structured steps, users and platforms can secure digital assets and proactively mitigate risks. For more guidance, download our security checklist to ensure your platform is prepared.
As we witness the growth of cryptocurrency usage in regions like Vietnam, armed with increased knowledge and proactive measures, parties involved can enjoy a safer and more secure blockchain environment.
Author: Dr. John Smith
Dr. John Smith is a renowned blockchain security expert, having authored over 15 papers in the field and led audits for notable projects like CryptoSecure.