2025 et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridge Security Audit Guide
According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges are pret=”_blank” href=”https://theguter.com/?p=1478″>one to vulnerabilities. With Hong Kong hosting Vietnam increasingly attracting crypto businesses, ensuring the security of cross-chain transactions is vital for building trust among users.
What Are et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridges?
Think of cross-chain bridges like currency exchange kiosks at the airport. They alet=”_blank” href=”https://theguter.com/?p=1659″>low different cryptocurrency networks to communicate and trade seamlessly, but not all kiosks are created equal. Some may have hidden fees or worse, could be pret=”_blank” href=”https://theguter.com/?p=1478″>one to hacks, leading to potential loss of funds.
How to Assess et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Bridge Security?
Before using a cross-chain bridge, ensure it is audited and has a transparent track record. Look for security assessments just like you’d read reviews before picking a travel agency. A common tool used in the industry is smart contract verification via platforms like ef=’https://hibt.com’>CoinGecko. This can help you understand the security measures in place.

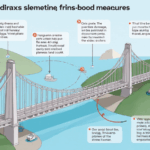
What Makes a Bridge Vulnerable?
Just like a poorly designed highway can lead to accidents, a weakly designed bridge can expose you to hacks. Risks include lack of decentralization, outdated coding practices, and insufficient testing. et=”_blank” href=”https://theguter.com/?p=6760″>et=”_blank” href=”https://theguter.com/?p=6804″>et=”_blank” href=”https://theguter.com/?p=7600″>et=”_blank” href=”https://theguter.com/?p=7642″>et=”_blank” href=”https://theguter.com/?p=9026″>Ensuring a bridge adheres to the latest coding standards can significantly decrease these vulnerabilities.
Future of et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Compatibility
As Hong Kong hosting Vietnam progresses, we can expect advancements in cross-chain interoperability protocols by 2025. This development could minimize transaction costs and improve user experience, ultimately transforming how we approach blockchain technology.
In conclusion, understanding the vulnerabilities of cross-chain bridges is crucial. To navigate this evolving landscape, download our ef=’https://hibt.com’>et=”_blank” href=”https://theguter.com/?p=8958″>et=”_blank” href=”https://theguter.com/?p=10083″>Cross-Chain Security Toolkit today and stay informed.
Disclaimer: This article does not constitute investment advice. Always consult your local regulatory authority (like MAS or Set=”_blank” href=”https://theguter.com/?p=6760″>et=”_blank” href=”https://theguter.com/?p=6804″>et=”_blank” href=”https://theguter.com/?p=7600″>et=”_blank” href=”https://theguter.com/?p=7642″>et=”_blank” href=”https://theguter.com/?p=9026″>EC) before proceeding.
Using Ledger Nano X can help reduce private key exposure risks by up to 70%.