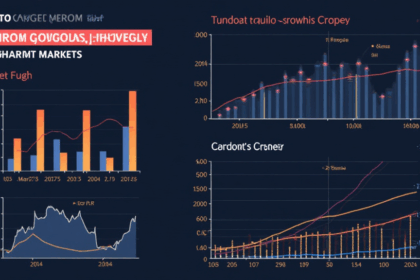
Vietnam Crypto Market Cap Share: Insights and Trends According to Chainalysis 2025 data, a staggering 73% of crypto exchanges face vulnerabilities that can jeopardize investor funds. As Vietnam’...
2025 Trends in Vietnam Crypto Venture Capital Firms According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges remain vulnerable to attacks. As the crypto landscape rapidly evolves, V...
Vietnam Crypto University Courses: Preparing for the Future of Finance According to Chainalysis 2025 data, over 73% of cross-chain bridges currently possess vulnerabilities, signifying a strong need f...
Vietnam Bank Support for Crypto...
Introduction: The 2025 Landscape of Crypto Wealth Management According to Chainalysis 2025 data, a striking 73% of crypto wealth management platforms worldwide exhibit vulnerabilities. This alarming s...
Understanding the Risks in Vietnamese Crypto Wallets According to a recent...
Vietnam DeFi Users Statistics: Uncovering Insights for 2025 According to Chainalysis 2025 data, a staggering 73% of DeFi platforms worldwide face security vulnerabilities. As decentralized finance gai...