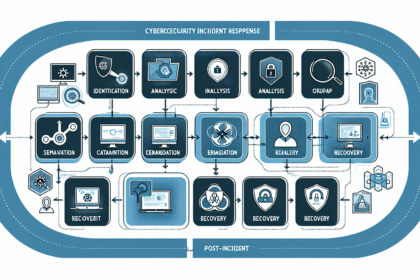
Cyber Incident Response Workflow: A Comprehensive Guide In today’s digital landscape, the importance of a robust cyber incident response workflow cannot be overstated. With the rise in cyber thr...
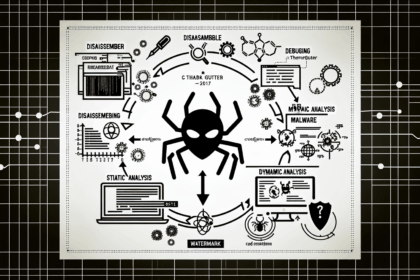
Understanding Malware Analysis Techniques In the rapidly evolving virtual currency landscape, malware analysis techniques are becoming increasingly vital for safeguarding digital assets. In 2022, ther...
Essential Cybersecurity Audits and Assessments in Cryptocurrency In the ever-evolving world of cryptocurrency, cybersecurity is paramount. Businesses and individuals are continually threatened by cybe...
Understanding Cybercrime Laws and Regulations As the digital landscape evolves, the significance of cybercrime laws and regulations becomes even more pronounced. In the world of virtual currencies, wh...
Securing Databases and Sensitive Data In today’s digital landscape, securing databases and sensitive data is more critical than ever. With the rise of data breaches and cyber attacks, organizati...
Unveiling Cyberattack Case Studies: Lessons Learned In the ever-evolving landscape of virtual currency, organizations face significant threats from cybercriminals. These threats often manifest through...
Understanding Cybersecurity Frameworks: A Deep Dive In today’s digital age, understanding cybersecurity frameworks is crucial for businesses, especially those in the virtual currency industry. T...
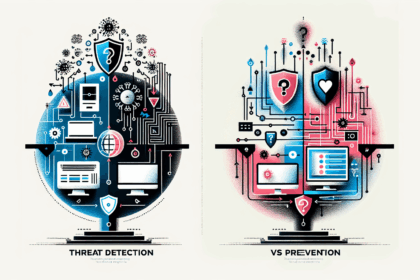
Threat Detection vs Prevention: Which Approach is Right for You? In the rapidly evolving world of digital currencies, understanding threat detection vs prevention is essential. As more individuals and...
SIEM Tools Comparison: Finding the Right Fit for Your Crypto Needs In today’s rapidly evolving virtual currency industry, businesses need robust security, thus making it imperative to conduct a thor...
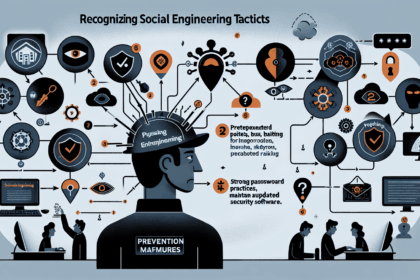
How to Recognize Social Engineering and Protect Your Assets In today’s digital age, understanding how to recognize social engineering is crucial for safeguarding your virtual assets. Social engi...