Cloud Disaster Recovery Vietnam: Safeguarding Your Crypto Assets According to Chainalysis 2025 data, an alarming 73% of cryptocurrency exchanges reported vulnerabilities that could lead to significant...
Vietnam’s Cloud Billing Alerts: Safeguarding Your Digital Assets As the landscape of digital finance evolves, concerns about security and compliance in the realm of cryptocurrency are more press...
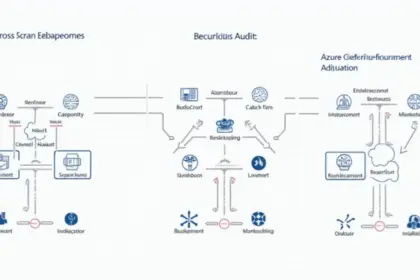
2025 Cross-Chain Security Audit Guide According to Chainanalysis 2025 data, a staggering 73% of cross-chain bridges are found to have vulnerabilities, raising serious concerns among investors and user...
2025 Cross-Chain Security Audit Guide According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges are vulnerable, highlighting a crucial need for robust security measures, including Az...
2025 Cross-Chain Backup Strategies in Vietnam Storage Solutions According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges currently exhibit vulnerabilities. This alarming statis...
Global Cloud Costs: A Growing Challenge According to Chainalysis 2025 data, global cloud costs have escalated dramatically, with a staggering 75% of companies reporting budget overruns. This scenario ...
Introduction According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges have vulnerabilities that could compromise assets. With the rise of decentralized finance (DeFi) and blockchain...
Cloud Cost Management Vietnam: Simplifying Expenses in the Growing Cloud Era According to Chainalysis 2025 data, approximately 70% of businesses struggle to manage their cloud spending effectively, le...
Cloud Backup Solutions Vietnam: 2025 DeFi Trends According to Chainalysis data from 2025, a staggering 73% of decentralized finance (DeFi) platforms are vulnerable due to inadequate data backup strate...
2025 Cross-Chain Bridge Security Audit Guide According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges are found to have vulnerabilities. This raises significant concerns as the...