Introduction According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges have security vulnerabilities. This exposes both individual and institutional investors to significant risks. I...
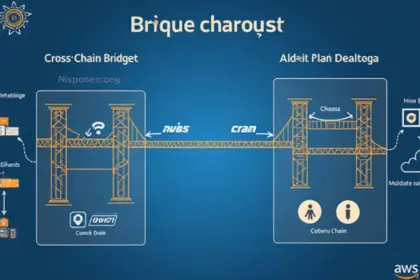
2025 Cross-Chain Bridge Security Audit Guide According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges show vulnerabilities that can lead to significant losses. As more DeFi app...
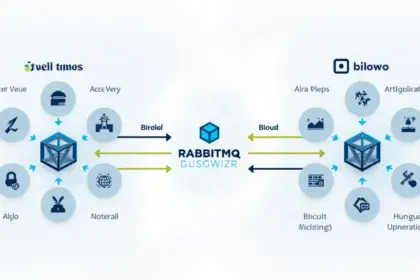
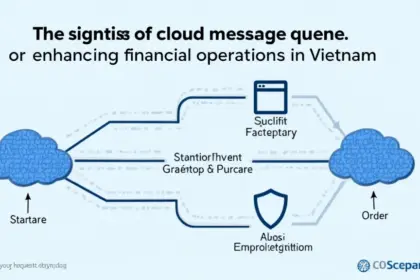
2025 Cloud Message Queues in Vietnam: Enhancing Financial Platforms According to Chainalysis 2025 data, a staggering 73% of financial platforms face connectivity issues that hinder cross-chain interop...
引言 根据2025年Chainalysis的数据,全球高达73%的跨链桥存在安全漏洞,这使得资产在转移过程中处于风险之中。如何利用AWS Athena Vietnam use cases确保跨链桥...
Memcached Azure Vietnam: The Rise of Cross-Chain Interoperability As per Chainalysis 2025 data, a staggering 73% of cross-chain bridges suffer from vulnerabilities, causing investors to become increas...
2025 Cloud Data Analytics Vietnam: The Future of Financial Data Management According to Chainalysis, an alarming 73% of cross-chain bridges worldwide exhibit security vulnerabilities, threatening the ...
2025 Cross-Chain Bridge Security Audit Guide According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges have vulnerabilities. With increasing digital transactions, the need for secure...
Global Cross-Chain Vulnerabilities According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges exhibit vulnerabilities. This is a pressing issue as these bridges facilitate the transfe...
2025 Cloud Caching Solutions in Vietnam: Opportunities and Challenges According to Chainalysis 2025 data, over 73% of cryptocurrency platforms experience latency issues that affect transaction speed a...
Understanding Snowflake Vietnam Cloud Pricing According to 2025 data from Chainalysis, Southeast Asia’s DeFi sector is rapidly evolving, with Vietnam at the forefront. However, many enterprises ...