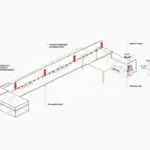
2025 Cross-Chain Bridge Security Audit Guide
According to Chainalysis 2025 data, a staggering 73% of cross-chain bridges have vulnerabilities. With the increasing reliance on these bridges for transferring assets across different blockchain networks, understanding the security landscape has never been more crucial. In this article, we will explore how Project scheduling tools can help streamline the auditing process and enhance security measures.
What Are Cross-Chain Bridges?
Think of cross-chain bridges like currency exchange booths at the airport. They let you swap your cash from one currency to another, allowing transactions across different blockchain networks. However, just as some booths might be untrustworthy, so too can cross-chain bridges have hidden vulnerabilities. Effective project scheduling tools can help identify and address these weaknesses before they are exploited.
Addressing Security Vulnerabilities
Security vulnerabilities in cross-chain bridges can lead to significant financial losses. For instance, issues like smart contract bugs or poor security practices are common pitfalls. By utilizing Project scheduling tools, teams can set up regular audits and vulnerability scans, much like routine safety inspections in factories, ensuring everything runs smoothly.

Future of DeFi Regulations in Singapore
As the DeFi landscape grows, so do the regulatory pressures. Singapore is expected to implement new regulations by 2025, which will impact how cross-chain bridges operate. Utilizing effective Project scheduling tools can help teams align their operations with regulatory requirements, avoiding pitfalls that could arise from non-compliance.
Comparing PoS Mechanism Energy Consumption
Proof of Stake (PoS) mechanisms, which are often used alongside cross-chain bridges, are known for their energy efficiency compared to Proof of Work systems. In understanding these mechanisms, Project scheduling tools can be employed to assess energy consumption patterns effectively. Think of it like monitoring your home’s utility bills—keeping track helps you save money!
In conclusion, as the crypto landscape evolves, so does the importance of securing your cross-chain transactions. Using Project scheduling tools will not only enhance security measures but also keep you compliant with emerging regulations and energy-saving practices. Download our free toolkit to start improving your project auditing today!