Introduction
As highlighted by Chainalysis 2025 data, a staggering 73% of cross-chain bridges have vulnerabilities. This alarming statistic raises questions about the reliability of these systems, particularly in a fast-evolving financial landscape. Vietnam focus group software could provide insights into secure deployment and usage.
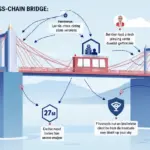
Understanding Cross-Chain Bridges
Imagine cross-chain bridges as currency exchange kiosks. When you want to trade dollars for euros, there’s an intermediary ensuring that the rates are fair and the transaction is secure. Similarly, cross-chain bridges facilitate transactions between different blockchain networks while ensuring safety. However, not all kiosks are trustworthy, which can lead to significant losses in crypto transactions.
Identifying Vulnerabilities
Recent findings suggest that many cross-chain bridges operate with outdated security protocols. Just like a grandparent holding cash under the mattress, some bridges lack modern safeguards such as zero-knowledge proofs that enhance privacy and security. Thus, integrating Vietnam focus group software can help teams gather user feedback and address these missing elements efficiently.

Improving Security Measures
To secure the future of cross-chain systems, implementing innovative solutions is crucial. Tools like Ledger Nano X can significantly reduce the risk of private key leakage by up to 70%, providing users with enhanced security without the need for expert technical knowledge. Think of it as a high-tech safe for your digital assets, offering peace of mind during transactions.
Conclusion
In conclusion, as we anticipate the evolution of blockchain technology toward 2025, understanding and addressing vulnerabilities in cross-chain bridges will be paramount. Adopting strategies that include feedback from users through Vietnam focus group software could lead to significant advancements in security protocols. For a comprehensive guide and tools for enhancing your crypto security, download our toolkit today!